The increasing digitisation of society means that, for most us, our identities are also becoming more digitised. Any personal data that exists online and can be traced back to you contributes to your “digital identity.” Everything from your social media profile to your online banking account contributes pieces of your digital identity.
Although the concept of digital identities is not new, it is becoming a growing source of concern in discussions around data privacy, and rightly so. Online, your personal data can be exploited by cyber criminals, big tech firms, and even the government. This vulnerability is the direct result of a larger issue: we don’t have control or ownership over our digital identities.
With our lives becoming more digitised, the question arises: is it possible to take back control of our data and our digital identities?
One potential solution may lie within the evolving concept of self-sovereign identity (SSI). SSI is a digital concept whereby an individual has ultimate control over his or her identity and is the final arbiter of who can access and use this data. The realisation of SSI has become possible in recent years thanks to advances in cryptography.
Since there is no universally accepted definition of SSI, various approaches to implementing a real-world SSI model have developed. One prominent approach depends on decentralised identifiers (DID), verifiable claims (VC) and other related standards from the World Wide Web Consortium (W3C), the internet standards organisation behind ubiquitous internet protocols like HTML and HTTPS.
First, users (aka owners, DID subjects) would need an identity wallet app on their smartphone or other device. This identity wallet is where an owner’s personal data is stored.
To get started, the wallet app would need to generate a public/private keypair without any third party participation. This keypair is used to represent a unique identifier number. With this identification number, owners would be able to make claims about their identity (e.g. “my name is Kiara and I am a US citizen”) and request digitally signed verifications of these claims from trusted issuing authorities (aka issuers or endorsers). A group of verified claims that are combined into a single document, such as a driver’s license, is known as a credential.
When the issuer signs a claim with their private key, a DID is created and stored in a form of verifiable data registry, such as a publicly available decentralised database or distributed ledger.
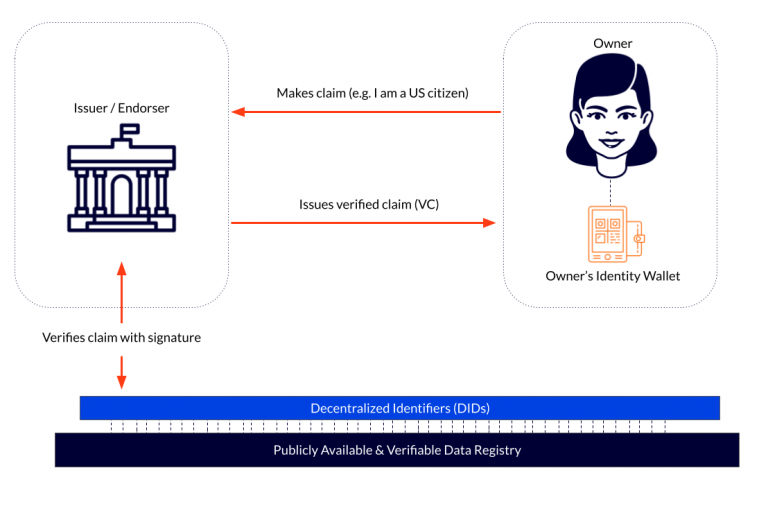 DIDs and and the presentation of VCs are under the complete control of the owner. This means that owners can decide which specific pieces of personal data they want to share with third parties.
DIDs and and the presentation of VCs are under the complete control of the owner. This means that owners can decide which specific pieces of personal data they want to share with third parties.
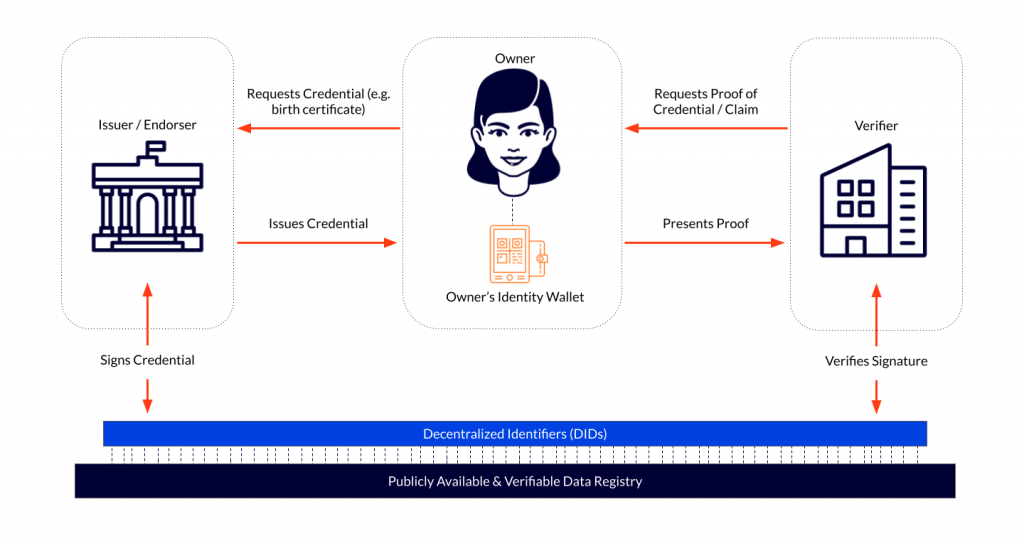
When an owner wants or needs to share certain VCs—such as one’s citizenship as part of a visa application, for example—they would send a cryptographically secure proof to the intended party for verification. This proof is based on the cryptographic link between the VC, the owner, and the issuer.
The verifying entity (aka verifier) would then verify the signatures of the proof. Digital signature verification is the part of the process enabled by public or private blockchain networks/DLTs.
There are seemingly endless use cases for a fully-realised SSI model. For example, SSI would streamline a number of current bureaucratic processes that require a string of manual, face-to-face, and paper processes associated with gathering and checking relevant identifying information, form-filling, query handling, and record keeping (think applying for a loan, or an immigration visa, or even a university program). You can then start to imagine how SSI would change the face of accessing a nearly endless range of goods and services.
The potential social impact of a well-developed SSI system is promising, though we must note that there are several key challenges to widespread SSI adoption:
We are likely years away from witnessing the full potential SSI use cases. However, as early SSI use cases develop and legal and political institutions evolve, the reality of impactful, integrated SSI systems becomes more tangible. One potential use case that could bring us closer to an SSI reality would be the need to digitally prove up-to-date vaccinations in a privacy-preserving way, in order to return to work, travel, etc.
Though we are still theorising what a future with SSI may look like, the SSI paradigm is one worth actively pursuing. Why? Because identity is at the core of establishing and building trust in a world characterised by remote interactions and faceless, digital transactions. Moreover, a working SSI model empowers the individual, putting each person in charge of their identity-related transactions, and personal information without having to rely on traditional, centralized authorities.
iov42 has always understood this connection between identity and trust, which is why we have spent the last 4 years architecting our identity-centric DLT platform. Identities are at the core of every use case we consider because we are determined to help create a digital society made up of interconnected groups that can fully trust one another.
By submitting your email you consent to receive iov42 newsletters by email. You can unsubscribe at any time. For further information, please see our Terms and Conditions and Privacy Policy
